CVE: CVE-2020-3801
Tested Versions:
- Acrobat DC version 2019.008.20064 (Windows 10 64-bit)
Product URL(s):
Description of the vulnerability
Adobe Acrobat is a family of application software and Web services developed by Adobe Inc. to view, create, manipulate, print and manage files in Portable Document Format (PDF).
Both Adobe Reader and Acrobat DC share the same AcroForm.api plugin:
File Version 19.012.20040.17853
Adobe Reader (and Adobe Acrobat DC) has a weird “feature” that leaks heap pointer after executes Javascript when openning XFA PDF. Any of these Javascript below would work.
xfa.form.myform.test.rawValue = xfa
xfa.form.myform.test.rawValue = {}
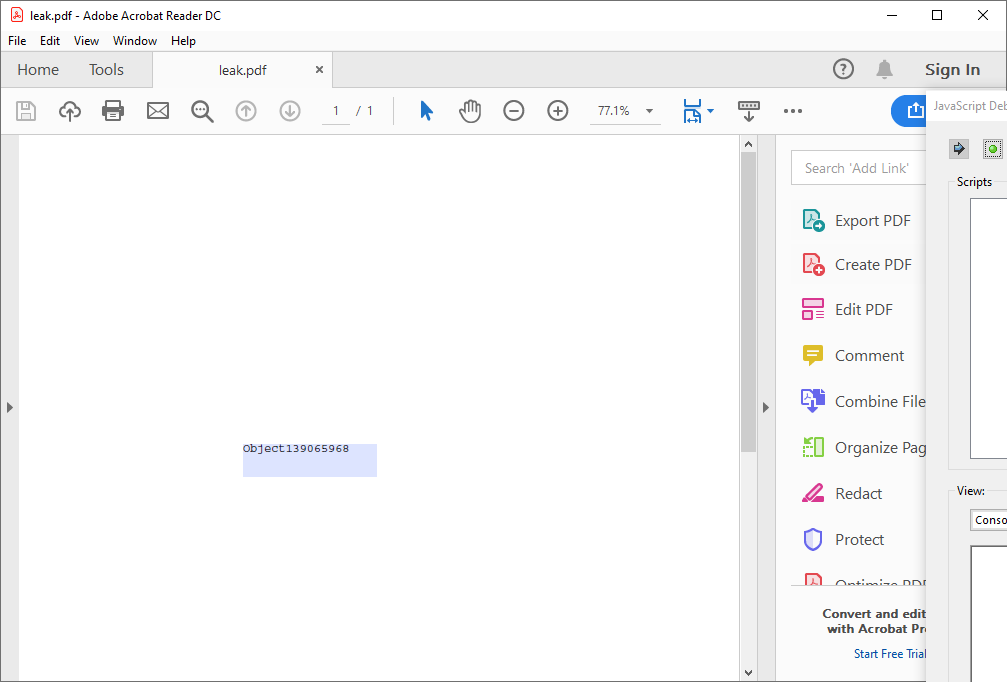
Checking with windbg shows that these are actual pointer values to the object that is assigned to rawValue.
The attacker can retrive the pointer value using rawValue after the assignment.
app.alert(xfa.form.myform.test.rawValue)
This bug might aid an attacker perform a successful attack when combined with a code execution vulnerability.
Timeline:
- 2020-02-04 Vendor disclosure
- 2020-03-17 Vendor patched
Vendor Response
The vendor has acknowledged the issue and released an update to address it.
The vendor’s advisory can be found here: APSB20-13.