Summary
| Product | Razer CentralService |
|---|---|
| Vendor | Razer |
| Severity | High - Adversaries may exploit software vulnerabilities to obtain privilege escalation. |
| Affected Versions | Razer Central 7.11.0.558 and below |
| Tested Versions | Razer Central 7.8.0.381 to 7.11.0.558 |
| CVE Identifier | CVE-2023-3513 |
CVSS3.1 Scoring System
Base Score: 7.8 (High)
Vector String: CVSS:3.1/AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H
| Metric | Value |
|---|---|
| Attack Vector (AV) | Local |
| Attack Complexity (AC) | Low |
| Privileges Required (PR) | low |
| User Interaction (UI) | None |
| Scope (S) | Unchanged |
| Confidentiality (C) | High |
| Integrity (I) | High |
| Availability (A) | High |
Product Overview
Razer Synapse 3 is a software suite developed by Razer, a leading gaming hardware manufacturer. It serves as a centralized hub for customizing and optimizing Razer peripherals, including keyboards, mice, headsets, and other gaming accessories. With its intuitive user interface, Synapse 3 allows gamers to personalize their devices by creating unique profiles, assigning macros, and fine-tuning settings such as lighting effects and DPI sensitivity. This software provides seamless integration with cloud storage, enabling users to access their personalized configurations from anywhere. With its advanced features and extensive compatibility, Razer Synapse 3 empowers gamers to enhance their gaming experience and gain a competitive edge.
Description of the vulnerability
One of these services is called RazerCentralService.exe, which acts as a central service for managing user information and notifications. Other applications can communicate with this service through a named pipe. However, there is a bug in RazerCentralService.exe that allows a user with low privileges to execute code as a system on a machine with RazerCentralService installed.
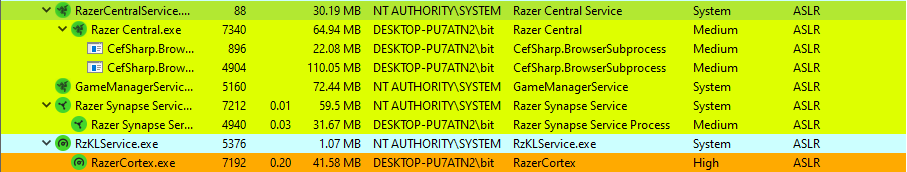
While analyzing Razer software, we found that a file called RazerCentralService.exe``, which runs under the SYSTEM`` account, tries to access a non-existent file located at the following path:
'C:\\ProgramData\\Razer\\Razer Central\\Accounts\\' + dirname +'\\Razer Central\\ConnectedAccounts\\ConnectedAccounts.bin'
The dirname variable represents a folder that begins with the prefix RZR_ followed by a series of hexadecimal characters. This folder is automatically generated once the user successfully logs into the system. Furthermore, we also verified the permissions assigned to the Razer Central folder.
s:\windows\razer>icacls "C:\ProgramData\Razer\Razer Central\Accounts\RZR_xxxxxxxxxxxxxxxxxxxx\Razer Central"
C:\ProgramData\Razer\Razer Central\Accounts\RZR_xxxxxxxxxxxxxxxxxxxx\Razer Central NT AUTHORITY\SYSTEM:(I)(OI)(CI)(F)
BUILTIN\Administrators:(I)(OI)(CI)(F)
CREATOR OWNER:(I)(OI)(CI)(IO)(F)
BUILTIN\Users:(I)(OI)(CI)(RX)
BUILTIN\Users:(I)(CI)(WD,AD,WEA,WA)
Successfully processed 1 files; Failed processing 0 files
Within this directory, we possess the flexibility to incorporate files or folders. Additionally, we hold the capability to substitute the ConnectedAccounts\ConnectedAccounts.bin file with our personalized iteration. This particular binary file is safeguarded through encryption, utilizing the AES-CBC algorithm. Notably, it employs a hardcoded key that conveniently facilitates both encryption and decryption operations.
def decrypt_ConnectedAccounts():
iv = "RZR_0280d8694a5582614c434074453e"[:16].encode('utf-8')
key = base64.b64decode("11Ir9bXYlDOU0xiKQszUlZ2N57TNS/GCAyLnZfj6Ibo=")
print (len(key)*8)
ciphertext = open(r"C:\ProgramData\Razer\Razer Central\Accounts\RZR_0280d8694a5582614c434074453e\Razer Central\ConnectedAccounts\ConnectedAccounts.bin", 'rb').read()
print ('===========')
cipher = AES.new(key, AES.MODE_CBC, iv)
plaintext = cipher.decrypt(ciphertext)
print (plaintext)
print ('================')
The code snippet below demonstrates the execution of a specific piece of code when the ConnectedAccounts.bin file undergoes deserialization using a binary formatter. This code is located within the AccountManager.dll module, which is loaded by the RazerCentralService.exe process.
private void Load()
{
try
{
SettingReadResult setting = this.m_settingsController.GetSetting("Razer Central", "ConnectedAccounts", "ConnectedAccounts.bin", SettingSource.Local, SettingSource.Undefined);
if (!setting.Success)
{
if (setting.ResultLocal == LoadResult.Failed_DataNotFound)
{
ConnectedAccountsManager.Logger.Info("No connected account credentials found.");
}
else
{
ConnectedAccountsManager.Logger.Error("Failed to load connected account credentials: " + setting.ResultLocal);
}
}
else
{
using (MemoryStream memoryStream = new MemoryStream(setting.Setting.Value))
{
Aes aes = Aes.Create();
aes.BlockSize = 128;
aes.KeySize = 256;
aes.Key = Convert.FromBase64String(ConnectedAccountsManager.m_keyString);
aes.IV = this.IV;
using (CryptoStream cryptoStream = new CryptoStream(memoryStream, aes.CreateDecryptor(), CryptoStreamMode.Read))
{
BinaryFormatter binaryFormatter = new BinaryFormatter();
this.m_credentials = (Dictionary<ConnectedAccount, ConnectedAccountCredentials>)binaryFormatter.Deserialize(cryptoStream);
}
}
}
}
catch (Exception exception)
{
ConnectedAccountsManager.Logger.Error("Exception loading connected account credentials", exception);
this.m_credentials = new Dictionary<ConnectedAccount, ConnectedAccountCredentials>();
this.Save();
}
}
By leveraging the power of ysoserial.net, we gain the ability to execute code with elevated privileges as the SYSTEM user. This process of deserialization occurs in two scenarios: when a user logs in or when the machine restarts. Moreover, we can also initiate the deserialization process by utilizing a named pipe. Notably, the RazerCentralService.exe grants read/write access to its pipe for all users.

pipe_name = r'\\.\pipe\{FC828A97-C116-453D-BD88-AD471496E03C}'
Here is a proof of concept (POC) written in Python 2 that you can use to execute notepad.exe as the SYSTEM user. Simply run the POC code provided here
Reproduction Steps
For simplicity, follow the following steps to re-produce.
- Install the Razer software.
- Install Python 2 and the necessary Python modules.
- Log in and wait for 3-5 minutes to ensure that the directory at
C:\ProgramData\Razer\Razer Central\Accountsexists. - Execute the exploit script using Python 2.
Conclusion
Having great power entails having great responsibility. When you operate as the SYSTEM user, you possess substantial power and carry significant responsibilities. Therefore, it is crucial to exercise caution in your actions. Additionally, it is important to understand that relying solely on an encrypted file with a hardcoded key does not guarantee security. To address any potential issues, you can follow the suggested steps outlined below:
- Avoid using binary formatter for deserialization.
- Ensure correct permissions are set for your namedpipe.
- Check your directory permissions.
Credits
Phan Thanh Duy (@PTDuy) of STAR Labs SG Pte. Ltd. (@starlabs_sg)